 Rabu, 8 Januari 2025 (01:33)
Rabu, 8 Januari 2025 (01:33)
 Music |
 Video |
 Movies |
 Chart |
 Show |
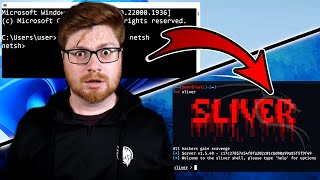 |
How Hackers Use netsh.exe For Persistence u0026 Code Execution (Sliver C2) (John Hammond) View |
 |
Persistence with Netsh Helper DLLs | Threat SnapShot (SnapAttack) View |
 |
Dumping Wi-Fi Credentials Using netsh (Professor K) View |
 |
How to Detect and Prevent Attacks Focused on Netsh-Based Exploits | Cybersecurity Monitoring (ULTIMATE THRILLER TV) View |
 |
Cyber Attacks on banking system | How to Mitigate with cmd (ULTIMATE THRILLER TV) View |
 |
Atomic Spotlight: Persistence with Command Process Auto Run Registry Key (Black Hills Information Security) View |
 |
Using Microsoft's netsh (The Technology Firm) View |
 |
Running a persistent Backdoor on hacked computer (MJB) View |
 |
How Hackers Evade Program Allowlists with DLLs (John Hammond) View |
 |
Video Blog: Using DLL Persist to Avoid Detection (TrustedSec) View |